kurtosis-tech /kurtosis
A platform for packaging and launching ephemeral backend stacks with a focus on approachability for the average developer.
Repository Statistics
Key metrics and engagement data
Timeline
Repository has been active for 2 years, 5 months
Repository Created
Last CommitRecently active
Stars
kurtosis-tech/kurtosis
⭐100
Want deeper insights? Explore GitObs.com
Languages
README.md

What is Kurtosis?
Have you ever tried to build on top of a colleague's work, or contribute to an open source project, just to get stuck on the first steps of spinning up a stack to play with? Kurtosis handles the complexity of spinning up ephemeral dev or test stacks so you can focus on developing, not configuring.
Kurtosis is formed of:
- A packaging system for distributing backend stack definitions, which can run on docker or on kubernetes
- A runtime with a per-stack file management system for reproducibly initializing the state of your stack
- A set of tools to enable devs to interact with their stacks, like they do on docker or k8s
Why use Kurtosis?
Kurtosis is best for:
- Reusing the logic in your stack definitions for all of: local dev, scheduled testing in CI, and ad-hoc larger-scale testing on k8s clusters
- Giving other devs a way to spin up your application, and commonly used variations of it, with one-liners, via Kurtosis' packaging and parameterization systems
- Handling complex setup logic in your backend stack, like passing arbitrary data between services as they start up, and enforcing arbitrary wait conditions
How is Kurtosis different than Docker Compose or Helm?
Kurtosis operates at a level higher than Docker Compose or Helm, and produces stacks running on either of the underlying engines (the Docker engine, or Kubernetes). Because of this additional layer of abstraction, we are able to introduce several features to improve the experience of spinning up ephemeral stacks:
- A per-stack file management system that enables portable state initialization for dev or test stacks
- Stack-level parameterizability; users have a powerful and flexible way (beyond messing with env vars) to affect modifications in their stacks
- First-class plug-and-play composability; it's expected for users to import stack definitions into larger stacks, and this experience is optimized
- The ability to get all of the above, but running over either the docker engine or k8s, at your election
NOTE: we do NOT recommend using Kurtosis to deploy long term production environments at this moment. Any issues/Discords related to production usage will be closed.
How do I get going?
To see Kurtosis in action, first install it using the instructions here.
Then, run the Redis voting app Kurtosis package:
bash1kurtosis run github.com/kurtosis-tech/awesome-kurtosis/redis-voting-app
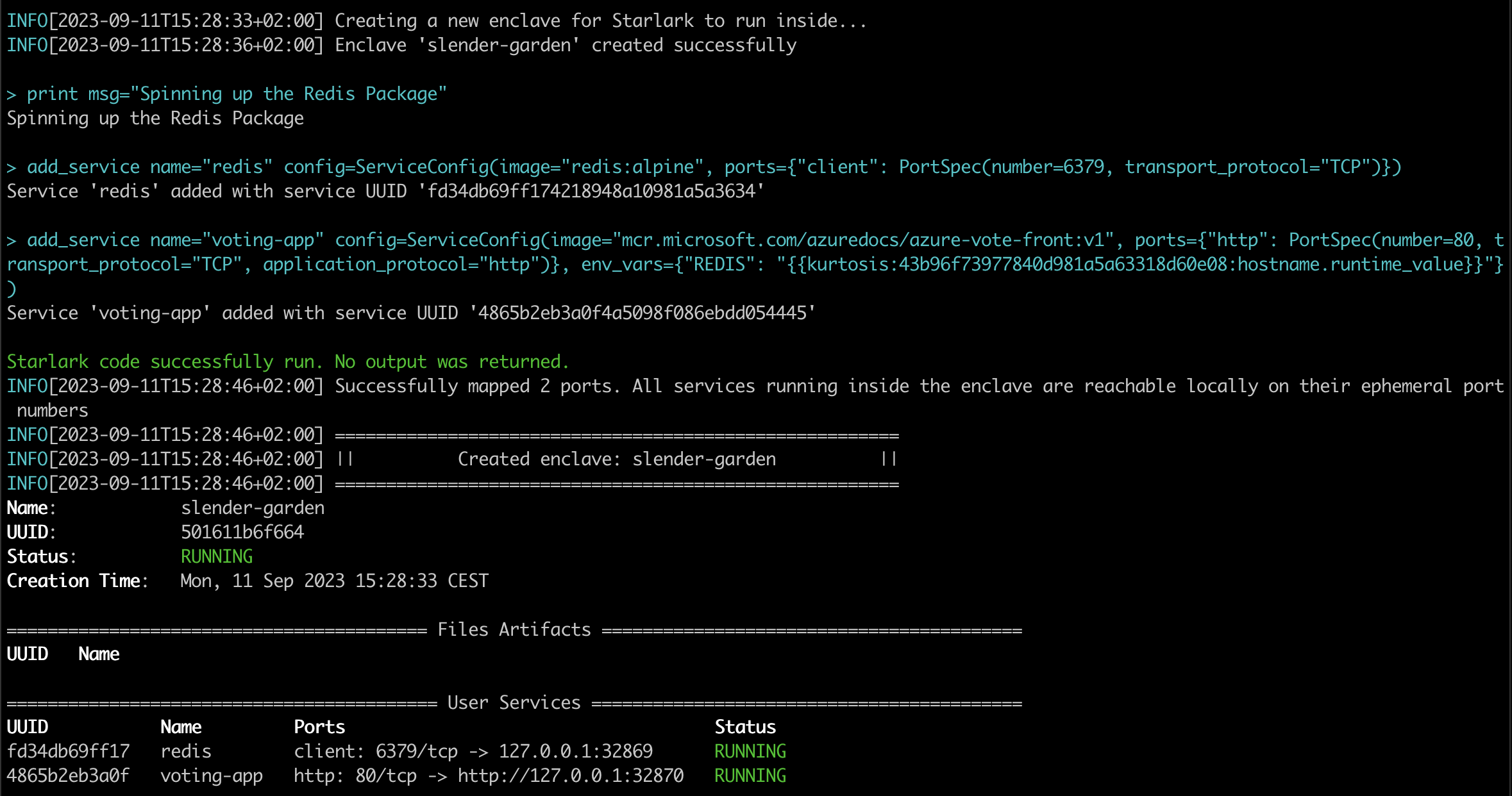
Finally, open the http link printed in the last line in your browser.
If you have an issue or feature request, we'd love to hear about it through one of the following:
- Post your question on our Github Discussions Forum
- Asking for help on our Discord server
- Filing an issue on our Github (which can also be done via
kurtosis feedback --bugorkurtosis feedback --feature) - Messaging us on Twitter
Going further
To try more Kurtosis packages just like this one, check out the awesome-kurtosis repo!
To learn about how to write Kurtosis packages, check out our quickstart.
To read about how Kurtosis works, see our documentation.
To see where we're going with the product, check out the roadmap here.
Got more questions? Drop them in our Github Discussions where we, or other community members, can help answer.
Contributing to Kurtosis
Expand to see contribution info
See our CONTRIBUTING file.
Repository Structure
This repository is structured as a monorepo, containing the following projects:
container-engine-lib: Library used to abstract away container engine being used by the enclave.core: Container launched inside an enclave to coordinate its stateengine: Container launched to coordinate enclavesapi: Defines the API of the Kurtosis platform (engineandcore)cli: Produces CLI binary, allowing interaction with the Kurtosis systemdocs: Documentation that is published to docs.kurtosis.cominternal_testsuites: End to end tests
Dev Dependencies (Nix)
Install the Nix package manager.
bash1sh <(curl -L https://nixos.org/nix/install)
And enable some Nix flags (alternatively you can add --extra-experimental-features 'nix-command flakes' every time calling the nix command):
bash1mkdir -p ~/.config/nix2echo "experimental-features = nix-command flakes" >> ~/.config/nix/nix.conf
And to bring the environment up, just open a new shell terminal, go to the root folder of the repo and run:
bash1nix develop
This will download all dev deps and setup the environment accordingly.
You can also use the direnv to automatically load the environment when entering the main folder or using a plugin in your preferred IDE:
vscode: mkhl.direnvjet brains: Direnv integration
Direnv can also be easily installed with Nix (or HomeBrew if you prefer):
bash1nix-env -f '<nixpkgs>' -iA direnv
Now you just to add the direnv hook to your shell:
bash1echo 'eval "$(direnv hook bash)"' >> ~/.bashrc2# or for ZSH3echo 'eval "$(direnv hook zsh)"' >> ~/.zshrc
Now next time you open a new shell terminal and go to repo's folder you environment will update and load automatically.
Dev Dependencies (Manual install)
The commands below assume that the env variable BREW_PREFIX contains the brew prefix.
bash1BREW_PREFIX="$(brew --prefix)"
Bash (5 or above)
On MacOS:
bash1# Install modern version of bash, the one that ships on MacOS is too old2brew install bash3# Allow bash as shell4echo "${BREW_PREFIX}/bin/bash" | sudo tee -a /etc/shells5# Optional: make bash your default shell6chsh -s "${BREW_PREFIX}/bin/bash"
Git
On MacOS:
bash1# Install modern version of git, the one that ships on MacOS can be too old2brew install git
Docker
On MacOS:
bash1brew install docker
Go (1.23 or above)
On MacOS:
bash1brew install [email protected]2# Add the Go binary dir to your PATH3PATH="${BREW_PREFIX}/opt/[email protected]/bin:$PATH"4# Add the GOPATH bin dir to your PATH5PATH="${HOME}/go/bin:$PATH"
On Ubuntu:
bash1wget https://go.dev/dl/go1.23.7.linux-amd64.tar.gz2tar -C /usr/local -zxf go1.23.7.linux-amd64.tar.gz3# Add the following to your bashrc or equivalent.4export PATH=$PATH:/usr/local/go/bin
Goreleaser
On MacOS:
bash1brew install goreleaser/tap/goreleaser
On Ubuntu:
bash1echo 'deb [trusted=yes] https://repo.goreleaser.com/apt/ /' | sudo tee /etc/apt/sources.list.d/goreleaser.list2sudo apt update3sudo apt install goreleaser
Node (20.* or above) and Yarn
On MacOS, using NVM:
bash1brew install nvm2mkdir ~/.nvm3nvm install 20.11.04npm install -g yarn
On Ubuntu, using NVM:
bash1curl https://raw.githubusercontent.com/creationix/nvm/master/install.sh | bash2source ~/.bashrc3nvm install 20.11.04npm install -g yarn
Rust
On MacOS, Ubuntu:
bash1curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
Go and Typescript protobuf compiler binaries
On MacOS:
bash1brew install protoc-gen-go2brew install protoc-gen-go-grpc3go install connectrpc.com/connect/cmd/protoc-gen-connect-go@latest4yarn global add ts-protoc-gen5yarn global add grpc-tools
On Ubuntu:
bash1go install google.golang.org/grpc/cmd/protoc-gen-go@latest2go install google.golang.org/grpc/cmd/protoc-gen-go-grpc@latest3go install connectrpc.com/connect/cmd/protoc-gen-connect-go@latest4yarn global add ts-protoc-gen5yarn global add grpc-tools
OpenAPI generators for Go and Typescript
On MacOS:
bash1go install github.com/deepmap/oapi-codegen/cmd/[email protected]2yarn global add [email protected]
On Ubuntu:
bash1go install github.com/deepmap/oapi-codegen/cmd/[email protected]2yarn global add [email protected]
Build Instructions
To build the entire project, run:
bash1./scripts/build.sh
Note: If you encounter module import errors related to github.com/kurtosis-tech/kurtosis/kurtosis_version, you may need to generate the version constants first:
bash1./scripts/generate-kurtosis-version.sh
This script generates the required kurtosis_version.go file that contains version constants used throughout the codebase. The file is automatically generated during the build process, but may need to be run manually in some development scenarios.
To only build a specific project, run the script on ./PROJECT/PATH/script/build.sh, for example:
bash1./container-engine-lib/scripts/build.sh2./core/scripts/build.sh3./api/scripts/build.sh4./engine/scripts/build.sh5./cli/scripts/build.sh
If there are any changes to the Protobuf files in the api subdirectory, the Protobuf bindings must be regenerated:
bash1./api/scripts/regenerate-protobuf-bindings.sh
If you are developing Kurtosis over a Podman cluster, run:
bash1./scripts/build.sh false true # no debug image, use podman
This will use the Podman image builder for building images. See documentation in scripts for more details on build options.
Running Dev Version
After building the project, run ./cli/cli/scripts/launch-cli.sh just like you would the kurtosis command. This will launch the latest locally built version of the CLI, which will also start the engine and core containers using their latest built images.
You can verify this by running ./cli/cli/launch-cli.sh engine status and
1A Kurtosis engine is running with the following info:2Version: 53d823 <-- or `-dirty` depending on the commit
The version will be identical to the version on the latest dev versions of the engine image created - (can verify with docker images). Enclaves started by the engine will be started with the same version as the engine.
If you'd like to specify a different core image version than that of the engine, you can do so with the --api-container-version flag on enclave add (e.g. ./cli/cli/scripts/build.sh enclave add --api-container-version <image tag>).
If you are working on multiple dev versions of the engine at a time, you can use engine restart --version <image tag> to specify exactly what version of the engine to use.
For frequent contributors, we recommend attaching an alias to kurtosis and ./cli/cli/scripts/launch-cli.sh.
bash1alias kt="kurtosis"2alias dkt="$(pwd)/cli/cli/scripts/launch-cli.sh"
If you want tab completion on the recently built CLI, you can alias it to kurtosis:
bash1alias kurtosis="$(pwd)/cli/cli/scripts/launch-cli.sh"2kurtosis enclave add
Unit Test Instructions
Build scripts also run unit tests as part of the build process.
For all Go modules, run go test ./... on the module folder. For example:
bash1cd cli/cli/2go test ./...
E2E Test Instructions
Each project's build script also runs the unit tests inside the project. Running ./script/build.sh will guarantee that all unit tests in the monorepo pass.
To run the end-to-end tests:
- Make sure Docker is running
console1$ docker --version2Docker version X.Y.Z
- Make sure Kurtosis Engine is running
console1$ kurtosis engine status2A Kurtosis engine is running with the following info:3Version: 0.X.Y
- Run
test.shscript
console1$ ./internal_testsuites/scripts/test.sh
If you are developing the Typescript test, make sure that you have first built api/typescript. Any
changes made to the Typescript package within api/typescript aren't hot loaded as of 2022-09-29.
Run Debug Instructions (for Golang code so far)
For running CLI with Golang remote debug:
- Build the CLI dev binary and run the command you want to debug (kurtosis version in this example), this will start the debug server and will wait for a client connection
bash1cli/cli/scripts/build.sh2source ./scripts/set_kt_alias.sh3ktdebug version
- Open the command's file you want to debug
- Add the breakpoint in the line where you want to stop the cursor
- Then choose the "CLI-remote-debug" run configuration in the "run panel"
- Press the "debug" button
- Use the debug panel to inspect the variables value and continue with the debug flow
For running CLI with Delve debug client:
- Build the CLI dev binary and run the command you want to debug (kurtosis version in this example), but first pass "dlv-terminal" as the first argument (this will start the Delve client in the terminal)
bash1cli/cli/scripts/build.sh2source ./scripts/set_kt_alias.sh3ktdebug dlv-terminal version
- You can add a new breakpoint using the terminal client and the
breakcommand
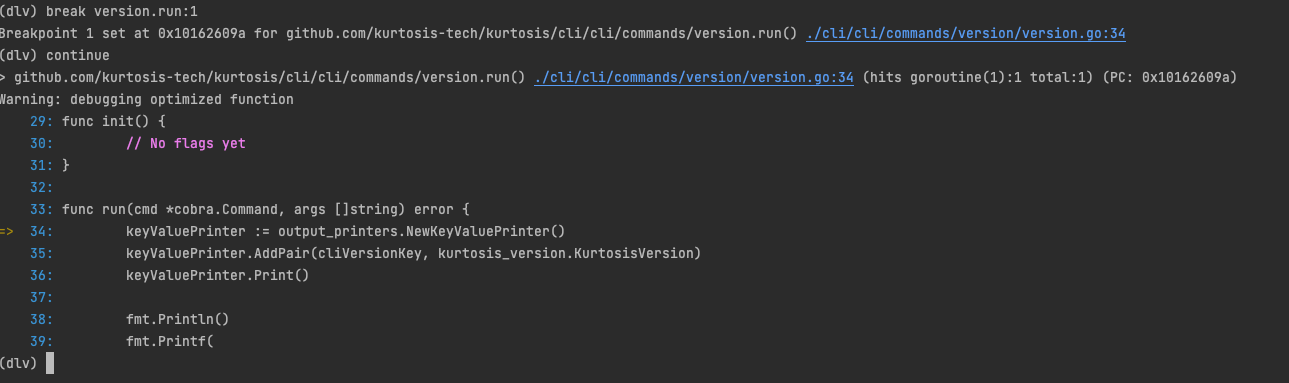
bash1(dlv) break version.run:1
- You can move the cursor to the breakpoint created in the previous step with the
continuecommand
bash1(dlv) continue
For running Kurtosis engine with Golang remote debug:
- Run the main build script with the first argument
debug_modeas true. This will generate a new Kurtosis engine container image which will contain thedebugsuffix in the name.
bash1scripts/build.sh true
- Add the breakpoint in the line where you want to stop the cursor
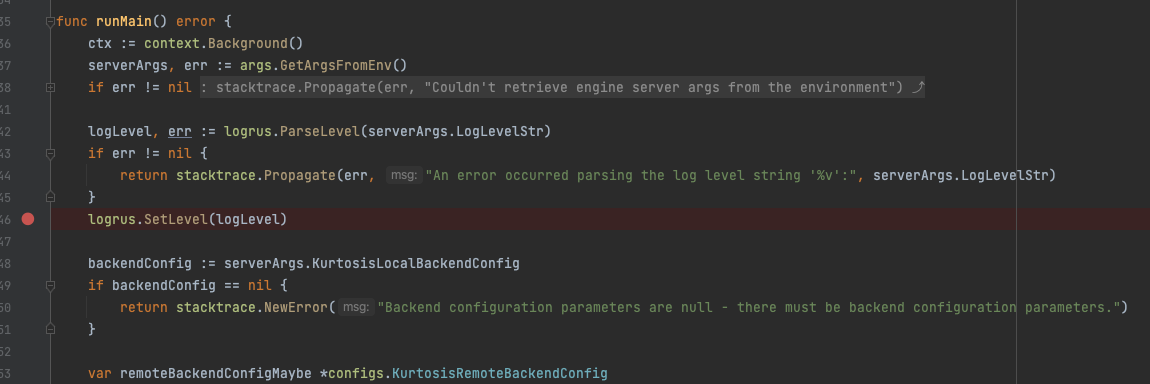
- Run the engine in debug mode with the
ktdev engine start --debug-modeor thektdev engine restart --debug-modecommands
bash1source ./scripts/set_kt_alias.sh2ktdev engine start --debug-mode
- Then choose the "Engine-remote-debug" run configuration in the "run panel"
- Press the "debug" button
- Make a call to the engine's server (you can use the Kurtosis CLI or Postman) in order to reach out the breakpoint in the code
- Use the debug panel to inspect the variables value and continue with the debug flow

- You can debug the CLI and the Kurtosis engine's server at the same time by running it with
ktdebuginstead ofktdevmentioned in a previous step, remember to run both remote debug configurations in the Goland IDE.
bash1source ./scripts/set_kt_alias.sh2ktdebug engine start
Additional steps if you are debugging Kurtosis engine in K8s:
- Upload the engine's image for debug to the K8s cluster
bash1# for example:2k3d image load kurtosistech/engine:5ec6eb-dirty-debug
- Run the port-forward script before pressing the debug button in Golang (in another terminal instance) to bind the host's port to the container's debug server port
bash1scripts/port-forward-engine-debug.sh
- Do not forget to run the Kurtosis gateway after calling the engine's server (in another terminal instance also)
bash1ktdev gateway
For running Kurtosis APIC with Golang remote debug:
- Run the main build script with the first argument
debug_modeas true. This will generate a new Kurtosis APIC container image which will contain thedebugsuffix in the name.
bash1scripts/build.sh true
- Add the breakpoint in the line where you want to stop the cursor.
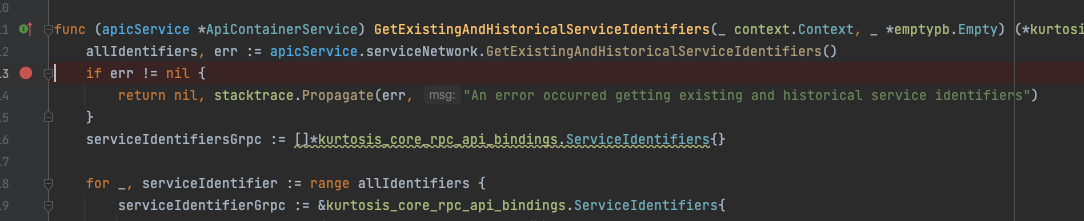
- Run the Kurtosis engine in debug more or not depending on if you want to also debug the engine.
bash1source ./scripts/set_kt_alias.sh2ktdev engine start --debug-mode34OR56ktdev engine start # you will have to build the engine in the regular way `engine/scripts/build.sh` if you choose this version
- Add a new enclave in debug mode with the
enclave addcommand and passing thedebug-modeflag. This will create a new APIC container with the debug server port bounded and waiting for a connection. IMPORTANT: You can only run one enclave in debug mode so far, if you want to run another one it will fail due the debug port is already in use,
bash1ktdev enclave add --debug-mode
- Then choose the "APIC-remote-debug" run configuration in the "run panel"
- Press the "debug" button
- Find the APIC's GRPC server port in the host machine (you can check it in Docker Desktop or using the Docker CLI, it's the one bounded with the container's 7443 port)
- Make a call to the APIC's server (you can use the Kurtosis CLI or Postman) in order to reach out the breakpoint in the code
- Use the debug panel to inspect the variables value and continue with the debug flow

- You can debug the CLI, the Kurtosis engine's server and the Kurtosis APIC's server at the same time by running it with
ktdebuginstead ofktdevmentioned in a previous step, remember to run the three remote debug configurations in the Goland IDE.
bash1source ./scripts/set_kt_alias.sh2ktdev engine start --debug-mode3ktdebug enclave add
Additional steps if you are debugging Kurtosis engine in K8s:
- Upload the APIC's image for debug to the K8s cluster
bash1# for example:2k3d image load kurtosistech/core:5ec6eb-dirty-debug
- Run the port-forward script before pressing the debug button in Golang (in another terminal instance) to bind the host's port to the container's debug server port
bash1scripts/port-forward-apic-debug.sh enclave-name
- Do not forget to run the Kurtosis gateway after calling the APIC's server (in another terminal instance also)
bash1ktdev gateway
Sponsoring Kurtosis
Kurtosis is an open source tool maintained by MAINTAINERS. If you find Kurtosis useful or use it for work, please consider supporting the continued development of Kurtosis. Thank you 🙏



